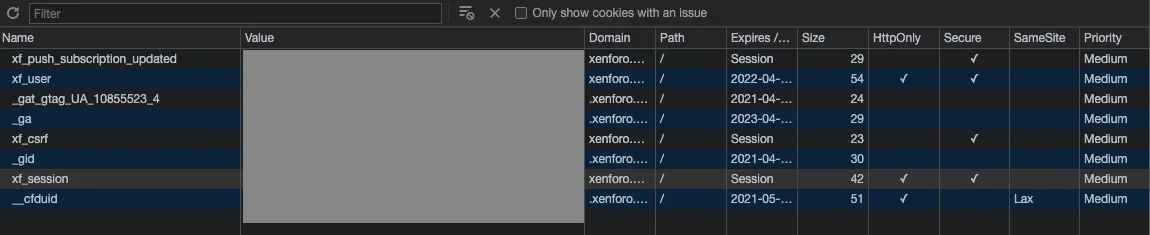
Why aren't the xf_user and xf_session cookies set to SameSite Lax? Assuming all forms are using POST then authentication cookies with the SameSite Lax value will not be sent for cross origin requests, eliminating the need for any anti-CSRF tokens at all.
Both Chrome and Firefox now automatically set cookies that don't specify a SameSite policy to SameSite Lax so I don't see why it isn't explicitly set?
 bugzilla.mozilla.org
bugzilla.mozilla.org
Is there a way to set these cookies to SameSite Lax and disable anti-CSRF tokens?
Both Chrome and Firefox now automatically set cookies that don't specify a SameSite policy to SameSite Lax so I don't see why it isn't explicitly set?
1604212 - Enable sameSite=lax by default on Nightly
RESOLVED (amarchesini) in Core - Networking: Cookies. Last updated 2021-12-31.
Is there a way to set these cookies to SameSite Lax and disable anti-CSRF tokens?
Last edited: