Hey,
Someone came on my website today,
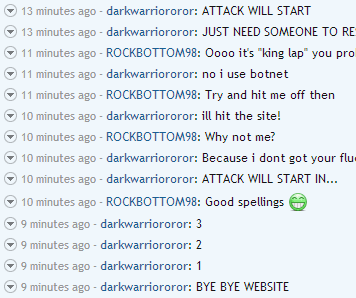
This isn't a new person, he regularly takes down the forums, but I have been neglecting it and he has gotten bored and tired of it. However the new moderator application format in and everyone rushed to the forums, and he took it down. No more neglecting this I need to fix this.
Zend_Db_Adapter_Mysqli_Exception: Too many connections - library/Zend/Db/Adapter/Mysqli.php:333
Generated By: Unknown Account,
Anyway when I googled this, a lot of people were replying to similar problems saying "that the traffic is too big" when this is nothing but an attack.
Anyway so what I think he is doing, is spam opening mysql connections untill the website goes down? when I restart apache the website briefly goes back online for 5 seconds.
So I need a way to limit mysql connections per ip or something along those lines. Is that the right way to fix this problem? Are there any negative effects in reducing the total connections per ip address? Can someone tell me exactly what to do? I am an expect.
Someone came on my website today,

This isn't a new person, he regularly takes down the forums, but I have been neglecting it and he has gotten bored and tired of it. However the new moderator application format in and everyone rushed to the forums, and he took it down. No more neglecting this I need to fix this.
Zend_Db_Adapter_Mysqli_Exception: Too many connections - library/Zend/Db/Adapter/Mysqli.php:333
Generated By: Unknown Account,
Anyway when I googled this, a lot of people were replying to similar problems saying "that the traffic is too big" when this is nothing but an attack.
Code:
Zend_Db_Adapter_Mysqli_Exception: Too many connections - library/Zend/Db/Adapter/Mysqli.php:333
Generated By: Unknown Account, Today at 7:26 AM
Stack Trace
#0 /home/squadcra/public_html/library/Zend/Db/Adapter/Abstract.php(315): Zend_Db_Adapter_Mysqli->_connect()
#1 /home/squadcra/public_html/library/XenForo/Application.php(719): Zend_Db_Adapter_Abstract->getConnection()
#2 [internal function]: XenForo_Application->loadDb(Object(Zend_Config))
#3 /home/squadcra/public_html/library/XenForo/Application.php(960): call_user_func_array(Array, Array)
#4 /home/squadcra/public_html/library/XenForo/Application.php(991): XenForo_Application->lazyLoad('db', NULL)
#5 /home/squadcra/public_html/library/XenForo/Application.php(1561): XenForo_Application::get('db')
#6 /home/squadcra/public_html/library/XenForo/Model.php(161): XenForo_Application::getDb()
#7 /home/squadcra/public_html/library/XenForo/Model/DataRegistry.php(138): XenForo_Model->_getDb()
#8 /home/squadcra/public_html/library/XenForo/Model/DataRegistry.php(97): XenForo_Model_DataRegistry->_getMultiFromDb(Array)
#9 /home/squadcra/public_html/library/XenForo/Dependencies/Abstract.php(147): XenForo_Model_DataRegistry->getMulti(Array)
#10 /home/squadcra/public_html/library/XenForo/FrontController.php(127): XenForo_Dependencies_Abstract->preLoadData()
#11 /home/squadcra/public_html/index.php(13): XenForo_FrontController->run()
#12 {main}
Request State
array(3) {
["url"] => string(22) "http://squadcraft.net/"
["_GET"] => array(0) {
}
["_POST"] => array(0) {
}
}Anyway so what I think he is doing, is spam opening mysql connections untill the website goes down? when I restart apache the website briefly goes back online for 5 seconds.
So I need a way to limit mysql connections per ip or something along those lines. Is that the right way to fix this problem? Are there any negative effects in reducing the total connections per ip address? Can someone tell me exactly what to do? I am an expect.