Lukas W.
Well-known member
we're currently having a client that is attempting to set up his external platform and XenForo installation, where his external page is situated on the main domain xyz.com and XenForo is located on the subdomain forums.xyz.com. We've configured the server to allow CORS requests to be allowed by now, so all scripts, stylesheets, etc. are loaded correctly.
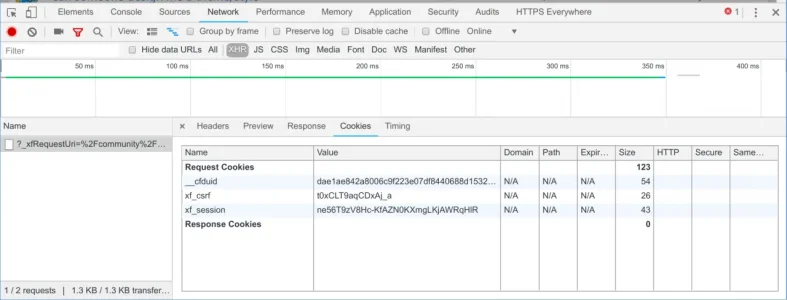
The issue we're currently stuck with is XenForo Ajax requests not passing through, as we constantly receive
we've also already tried to change the domain to
Any idea why we continue to receive this error on all Ajax calls (such as login dropdown, etc.)?
The issue we're currently stuck with is XenForo Ajax requests not passing through, as we constantly receive
Cookies are required to use this site. You must accept them to continue using the site. errors. The cookies are currently configured as follows:
Code:
'prefix' => 'xf_',
'path' => '/',
'domain' => '.xyz.com'we've also already tried to change the domain to
xyz.com and forums.xyz.com with the same effect. Cookies seem to be carried over correctly, meaning if we log into XenForo on forums.xyz.com and then switch to the external page on xyz.com, cookies remain set and the user is still logged in.Any idea why we continue to receive this error on all Ajax calls (such as login dropdown, etc.)?