You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
[TAC] Fool Bot Honey Pot [Paid] 3.0.32
No permission to buy ($29.00)
- Thread starter tenants
- Start date
tenants
Well-known member
Okay, so stable! stay that way damned it .... trying to get this to be my last post on this thread for a while:
Okay, I'm stopping with fbhp updates for a while now.
It's stable, works and picks up the new wave of js enabled bots that bypass the core honeypots, bypass the reg timer and don't get detected by APIs..... my job here is once again done (hopefully the core wont copy again).
Tenants:2 SpamBots:0
If you find a bug, or see a bot get through, let me know, send me the fingerprint and I'll update it.... other than that, I don't believe it needs anymore work.
View attachment 149951 View attachment 149952View attachment 149953View attachment 149954
jondoe0069
Member
okay, no issues on install now then?
I'll send it out to the packs quickly
It installed and seems to be working as expected.
Thanks again!
Mouth
Well-known member
Interesting behaviour ...
... spammer used an automated tool, which was picked-up and failed. Then one min later, registered manually (or bypassed FPHB), and successfully registered.
Code:
No Bot Triggers Found
FoolBotHoneyPot: Detected As Human - Registration Allowed
Tuesday at 02:01 : 49.35.15.86:41486
Username: Ams khan
Email: Amskhan007@gmail.com
Host: 49.35.15.86
User Agent: Mozilla/5.0 (Linux; Android 7.0; Moto G (4) Build/NPJ25.93-14) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/56.0.2924.87 Mobile Safari/537.36
Time taken to register: 18 (seconds)
JavaScript Enabled Browser: TRUE
Core Classical Honeypots: 0
FBHP Classical Honeypots: 0
Basic Proxy Detection: Possibly Forged IP Address, ipAddress (49.35.15.86) == ReverseDNS (49.35.15.86)
Browser Plugins Detected: None
Hidden Fields Modifed,
FoolBotHoneyPot: Detected As A Bot - Registration Blocked
Tuesday at 02:00 : 49.35.15.86:41486
Username: Amskhan007
Email: Amskhan007@gmail.com
Host: 49.35.15.86
User Agent: Mozilla/5.0 (Linux; Android 7.0; Moto G (4) Build/NPJ25.93-14) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/56.0.2924.87 Mobile Safari/537.36
Time taken to register: 84 (seconds)
JavaScript Enabled Browser: TRUE
Core Classical Honeypots: 0
FBHP Classical Honeypots: 1
Basic Proxy Detection: Possibly Forged IP Address, ipAddress (49.35.15.86) == ReverseDNS (49.35.15.86)
Browser Plugins Detected: None... spammer used an automated tool, which was picked-up and failed. Then one min later, registered manually (or bypassed FPHB), and successfully registered.
tenants
Well-known member
Interesting behaviour ...
Code:No Bot Triggers Found FoolBotHoneyPot: Detected As Human - Registration Allowed Tuesday at 02:01 : 49.35.15.86:41486 Username: Ams khan Email: Amskhan007@gmail.com Host: 49.35.15.86 User Agent: Mozilla/5.0 (Linux; Android 7.0; Moto G (4) Build/NPJ25.93-14) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/56.0.2924.87 Mobile Safari/537.36 Time taken to register: 18 (seconds) JavaScript Enabled Browser: TRUE Core Classical Honeypots: 0 FBHP Classical Honeypots: 0 Basic Proxy Detection: Possibly Forged IP Address, ipAddress (49.35.15.86) == ReverseDNS (49.35.15.86) Browser Plugins Detected: None Hidden Fields Modifed, FoolBotHoneyPot: Detected As A Bot - Registration Blocked Tuesday at 02:00 : 49.35.15.86:41486 Username: Amskhan007 Email: Amskhan007@gmail.com Host: 49.35.15.86 User Agent: Mozilla/5.0 (Linux; Android 7.0; Moto G (4) Build/NPJ25.93-14) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/56.0.2924.87 Mobile Safari/537.36 Time taken to register: 84 (seconds) JavaScript Enabled Browser: TRUE Core Classical Honeypots: 0 FBHP Classical Honeypots: 1 Basic Proxy Detection: Possibly Forged IP Address, ipAddress (49.35.15.86) == ReverseDNS (49.35.15.86) Browser Plugins Detected: None
... spammer used an automated tool, which was picked-up and failed. Then one min later, registered manually (or bypassed FPHB), and successfully registered.
Can I see the fingerprint for this one
4 possibilities
1) its a human tampering with the fields (someone nosy, looking at the markup and wondering what the hidden fields do)
2) it a bloody bot, field trial and error (why it only got picked up by one hp on 1st attempt is worrying ... this might be a hp that I should duplicate to make sure they get locked out on 1st attempt)
3) its a user using a pw logger that we haven't picked up on yet
4) semi automation that was turned off on re-attempting
- the fact that they possibly forged their IP address is suspicious
- I wouldn't expect browser plugins on mobiles/Android, so this does not point either way
- they haven't changed their IP on reattempting (or even their email), bots usually do change this to avoid getting re-detected.
It's an Indian ip address (although possibly forged), I'm suspecting a form filler / semi automation on a mobile (cheap posting, real human with tools that make the job quick)
I should know more with the fingerprint.
Last edited:
Mouth
Well-known member
Sent.Can I see the fingerprint for this one
tenants
Well-known member
Ah.... thats much nicer when it flashes and tells you the exact type of bot fbhp detects, I'm happy with that. Thanks bots for stepping up your game, I'm using your tools and power against you're selves 
It's interesting that UBot manages to fake browser plugins, maybe the browser they are automating actually has plugins, which seems a bit heavy (I would usually choose a much lighter browser).
Still, you can see that even UBot is now bypassing all core mechanisms
Gets caught by fbhp
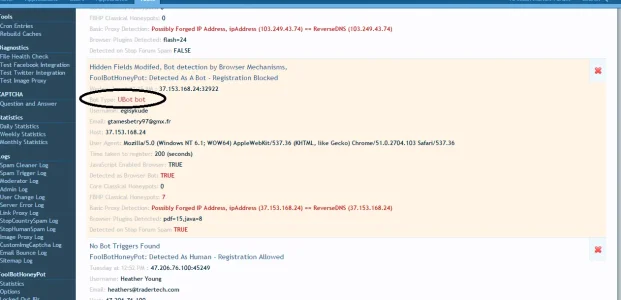
Hmmm, there's some very interesting fingerprint data from this ubot log
It's interesting that UBot manages to fake browser plugins, maybe the browser they are automating actually has plugins, which seems a bit heavy (I would usually choose a much lighter browser).
Still, you can see that even UBot is now bypassing all core mechanisms
- Bypasses the core reg timer (200 seconds, these bots are definately slowing on purpose)
- Bypasses the core honeypots
Gets caught by fbhp
- From friging direct detection! Detection doesn't get better than that
- fbhp honeypots
- a general browser based bot detection

Hmmm, there's some very interesting fingerprint data from this ubot log
Last edited:
tenants
Well-known member
It removes them when new bots try to register
There's not point in creating overhead from using crons job to clear these accounts up at exactly the right second/minute
- So "will be removed at" is not a strict time, but usually that time or 5-10 minutes later (depending on the frequency of bots)
-- the next time a bot gets added to that list, those ones that have expired will be pushed off, so the bots do the overhead / work, users don't, and there's no cron job overhead
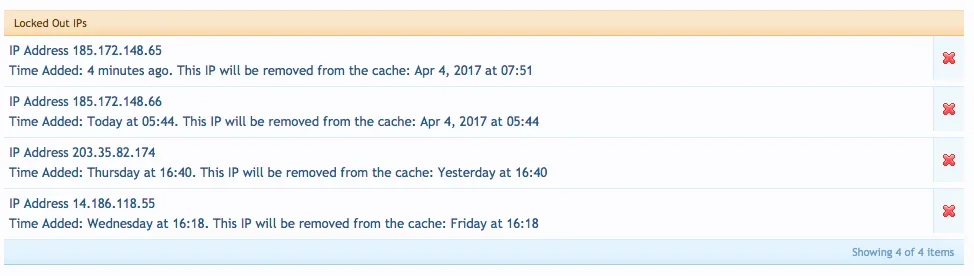
It possibly implies no bots have recently attempted (lucky you)
Are they really the only bots in your cache??? Usually people have 30 - 100
There's not point in creating overhead from using crons job to clear these accounts up at exactly the right second/minute
- So "will be removed at" is not a strict time, but usually that time or 5-10 minutes later (depending on the frequency of bots)
-- the next time a bot gets added to that list, those ones that have expired will be pushed off, so the bots do the overhead / work, users don't, and there's no cron job overhead
It possibly implies no bots have recently attempted (lucky you)
Are they really the only bots in your cache??? Usually people have 30 - 100
Last edited:
Mouth
Well-known member
Yes, they're the only ones.It possibly implies no bots have recently attempted (lucky you)
Are they really the only bots in your cache??? Usually people have 30 - 100
tenants
Well-known member
I've already added an option to add password managers to avoid, but it's not that intuitive.
I'll add a method to clear hp passwords next version via javascript. The classical honeypots are less important than they used to be, so they're not that important, avoiding false positives it far more critical (fbhp has many other methods than classical honey pots)
This means, js enabled bots will get around the classical honey pots... BUT THEY WERE ANYWAY, that is why I've re-released this plugin with many other methods
The non js enabled bots will still get caught
and... it will avoid password managers without the need of admins having to do anything to the options
I'll add a method to clear hp passwords next version via javascript. The classical honeypots are less important than they used to be, so they're not that important, avoiding false positives it far more critical (fbhp has many other methods than classical honey pots)
This means, js enabled bots will get around the classical honey pots... BUT THEY WERE ANYWAY, that is why I've re-released this plugin with many other methods
The non js enabled bots will still get caught
and... it will avoid password managers without the need of admins having to do anything to the options
Last edited:
tenants
Well-known member
tenants updated FoolBotHoneyPot Bot Killer: Spam Combat with a new update entry:
Added an option to avoid all Password Managers
This option will clear all Hidden Password and Username fields using javasript before form submission. This means all bots that are JS enabled will never get detected by the classical FBHP honey pots (but may get detected by other FBHP mechanisms, THERE ARE MANY). Ticking this option will ensure password managers are never caught by FBHP classical honeypots
-- This option is switched off by default in the options area of FBHP
-- This was in the original FBHP, it was removed since the core coppied the old classical honeypot methods but missed this out (did it poorly and missed many other fbhp things out too). Hence, the core will always catch password managers (FBHP avoided them in the past, and can avoid them again by just ticking this option)
If you still find the core catches password managers
1) report this to xenforo (it is a xenforo bug that has been in xenforo for some time)
2) let me know, I should be able to fix their issue in fbhp too
Read the rest of this update entry...
Added an option to avoid all Password Managers
This option will clear all Hidden Password and Username fields using javasript before form submission. This means all bots that are JS enabled will never get detected by the classical FBHP honey pots (but may get detected by other FBHP mechanisms, THERE ARE MANY). Ticking this option will ensure password managers are never caught by FBHP classical honeypots
-- This option is switched off by default in the options area of FBHP
-- This was in the original FBHP, it was removed since the core coppied the old classical honeypot methods but missed this out (did it poorly and missed many other fbhp things out too). Hence, the core will always catch password managers (FBHP avoided them in the past, and can avoid them again by just ticking this option)
If you still find the core catches password managers
1) report this to xenforo (it is a xenforo bug that has been in xenforo for some time)
2) let me know, I should be able to fix their issue in fbhp too
Read the rest of this update entry...
Last edited:
Mouth
Well-known member
Nervously, just tested my site and registration is working fine.There may be a bug with this. Can it be that it also clears the real password field? My users are no longer getting through the registration as they are getting the invalid password error.
I updated to the last version ~24 hrs ago.
Mouth
Well-known member
Ahh, no. 'Avoid All Password Managers' is unticked.Did you activate the password manager setting?
Similar threads
- Replies
- 10
- Views
- 2K
- Replies
- 10
- Views
- 2K
- Replies
- 2
- Views
- 2K
- Replies
- 0
- Views
- 1K
- Question
- Replies
- 3
- Views
- 2K